Do you Self-host PostHog?
If so, you should inspect the Network tab while visiting your dashboard, You’ll find a bunch of requests to different posthog.com domains.
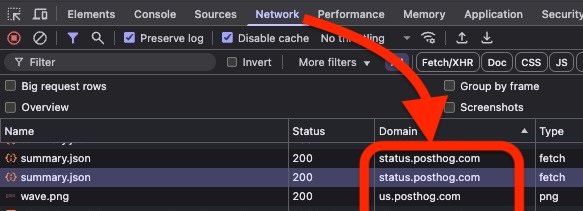
These requests seem to harmless – loading assets, getting service status ( e.g. https://status.posthog.com ).Some appear to be for pulling telemetry and usage data of dashboard users – likely geared at enterprise users on paid instances. One in particular ( evil.posthog.com 🤨 ) just looks suspicious.
If you’re self-hosting for privacy reasons, it’s a good idea to block these requests..
The two places we’ll want to block these requests are in…
- Your server ( easy )
- Your instance admin and site visitors browsers ( difficult )
Blocking PostHog server calls
An easy way to prevent to prevent your server from phoning PostHog, is to point all requests back to your own server.
Simply add the following block to /etc/hosts.
# No PostHog phone home
127.0.0.1 40hogflix.posthog.com
127.0.0.1 app.posthog.com
127.0.0.1 app-static-prod.posthog.com
127.0.0.1 billing.posthog.com
127.0.0.1 cdn2.posthog.com
127.0.0.1 cdn.posthog.com
127.0.0.1 docs.posthog.com
127.0.0.1 eu.i.posthog.com
127.0.0.1 eu.posthog.com
# 😱
127.0.0.1 evil.posthog.com
127.0.0.1 hogflix.posthog.com
127.0.0.1 internal-j.posthog.com
127.0.0.1 license.posthog.com
127.0.0.1 mcp.posthog.com
127.0.0.1 .posthog.com
127.0.0.1 something.posthog.com
127.0.0.1 status.posthog.com
127.0.0.1 test.posthog.com
127.0.0.1 the.posthog.com
127.0.0.1 us.i.posthog.com
127.0.0.1 us.posthog.comThis list of domains is what I managed to find as of the time of writing, but in future you may need to add others, to find more references, search for them in the PostHog/posthog project.docker-compose exec web grep -r -o '[a-zA-Z0-9.-].posthog.com' /code --include=".py" | cut -d: -f2 | sort -ub
Blocking browser calls to posthog.com
To block clients/browsers from loading *.posthog.com domains.
You will need to …
- Add a step in the project Dockerfile to replace all *.posthog.com domains with your own instance domain.
- Build a custom posthog/posthog image using the replaced file and update all the containers are using that image.
- Set
REGISTRY_URLin the .env file to your custom image name.
- Set
- Load (
init) PostHog javascript object with the option –disable_external_dependency_loading: true
That’s all! now all your analytics data belongs solely to you. and PostHog
☕ Was this helpful?
If this guide helped you to be more secure, say thanks with a coffee:

0 responses to “Block PostHog telemetry on self-hosted”